Is PCI DSS 3.2 an incompatible truth with contactless payment cards and an inconvenient truth for Banks and card issuers?
The following is an interpretation of the Payment Card Industry Data Security Standard version 3.2 (PCI DSS 3.2) against the data readily accessible from a contactless card.
It suggests that your card data is at risk, that this risk is identified as a concern for the PCI (Payment Card Industry) such that they list it as a key concern. Yet contactless cards offer no protection of this data and the PCI does not seem to address this.
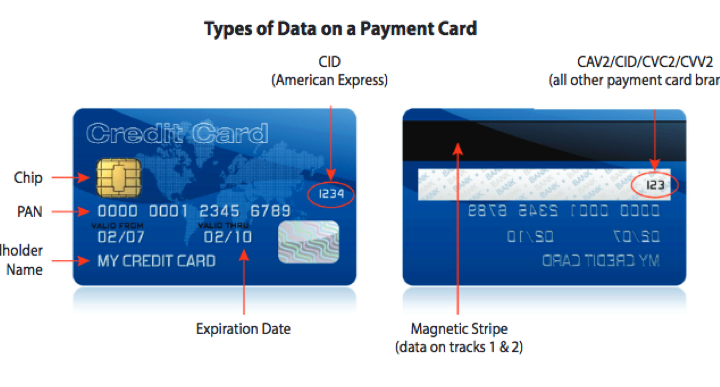
All the different data types stored on a bank card including chip, PAN, Cardholder name expiration date magnetic strip
Activities that put data at risk
A survey by Forrester Consulting of businesses in the U.S. and Europe reveals activities that may put cardholder data at risk.
- 81% store payment card numbers.
- 73% store payment card expiration dates.
- 71% store payment card verification codes.
- 57% store customer data on the payment card magnetic strip.
- 16% store other personal data.
Source: The State of PCI Compliance (commissioned by RSA/ EMC)
What are the PCI CONCERNS and it’s role?
The goal of the PCI Data Security Standard (PCI DSS) is to protect cardholder data and sensitive authentication data wherever it is processed, stored or transmitted. The security controls and processes required by PCI DSS are vital for protecting all payment card account data, including the PAN – the primary account number printed on the front of a payment card.
What does PCI Data Security Standard (PCI DSS) do? Cardholder data protection
Cardholder data refers to any information printed, processed, transmitted or stored in any form on a payment card. Entities accepting payment cards are expected to protect cardholder data and to prevent its unauthorized use – whether the data is printed or stored locally or transmitted over an internal or public network to a remote server or service provider.
Paragraph 3.3 of PCI DSS 3.2 states that Mask PAN when displayed (the first six and last four digits are the maximum number of digits you may display), so that only authorized people with a legitimate business need can see more than the first six/last four digits of the PAN. This does not supersede stricter requirements that may be in place for displays of cardholder data, such as on a point-of-sale receipt.
Paragraph 3.4 states that Render PAN unreadable anywhere it is stored – including on portable digital media, backup media, in logs, and data received from or stored by wireless networks. Technology solutions for this requirement may include strong one-way hash functions of the entire PAN, truncation, index tokens with securely stored pads, or strong cryptography. (See PCI DSS Glossary for the definition of strong cryptography).
But by comparison, the riskiest behavior is using contactless cards with RFID chips and the contactless payment favoured by banks as the alternative to cash. Why? Simply because all contactless payment cards natively and openly reveal basic information that should be protected, the PAN, and other data. With a mobile phone application, currently available to download, it is very simple to access (without the cardholder’s knowledge or permission) the data from contactless cards.
What data can be found reading a credit card?
I want to show you the results of reading the card from one phone application. In the App, the card number is revealed in full, but in line with PCI guidelines, only the first six and last four digits are revealed here.
- Track 1
- Expiry date: 1 Nov 2017
- PAN Card number : 540463******8991
- Format : B
- Service: International interchange
- Normal
- No restrictions
- None
- Track 2
- Expiry date: 1 Nov 2017
- PAN Card number : 540463******8991
- Service: International interchange
- Normal
- No restrictions
- None
- AID : A0 00 ** ** ** 10 10
- Label: MasterCard
- Priority: 1
- Pin try left: 3 Time(s)
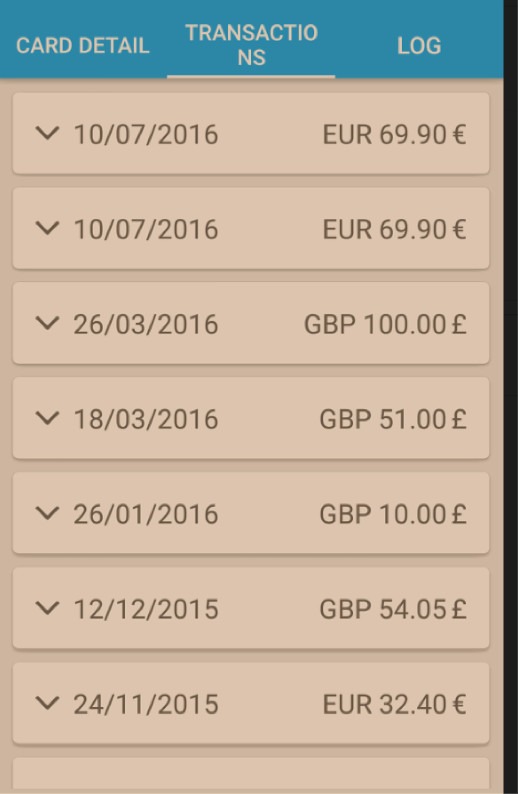
Not only this, but it is also possible to view the recent transaction log of the card.
According to PCI DSS 3.2, none of this information should be accessible, transmissible, recordable or stored and yet all of it is. So when it comes to risky behaviour should not the guide address and highlight this as follows: 100% of contactless cards reveal PAN and other sensitive customer data in breach of PCI DSS 3.2 when accessed.
What about Governance?
It is said that “all five payment card brands, along with Strategic Members, share equally in the Council’s governance, have equal input into the PCI Security Standards Council and share responsibility for carrying out the work of the organization”. And “PCI DSS applies to All entities involved in payment card processing including merchants, processors, acquirers, issuers and service providers”.
So one must surely ask where’s the excuse for this seemingly non-compliance with DSS 3.2? How can a merchant be held accountable to DSS 3.2 when the governing members appear not to be? Ask yourself as a card user, are you fully satisfied that your contactless payment card is truly secure, that your data is not of use to fraudsters?
And what does this lack of security ultimately benefit? It would seem only the ease and speed of use of contactless transactions perhaps to ensure contactless payment uptake? Complying with PCI DSS Standards, is that not the primary concern?
‘We have written many articles about security issues with contactless cards. You can read about this in our blog



0 Comments